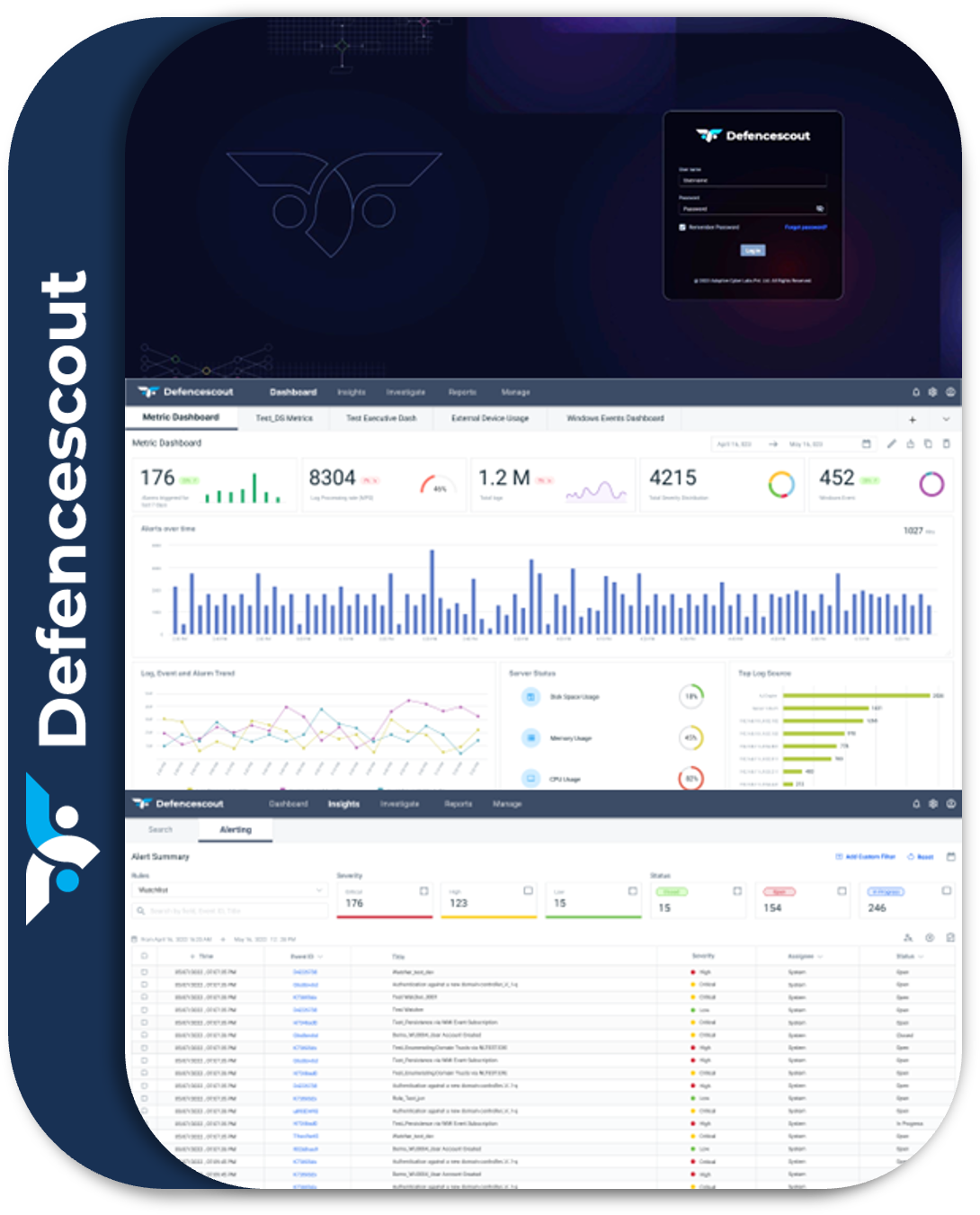
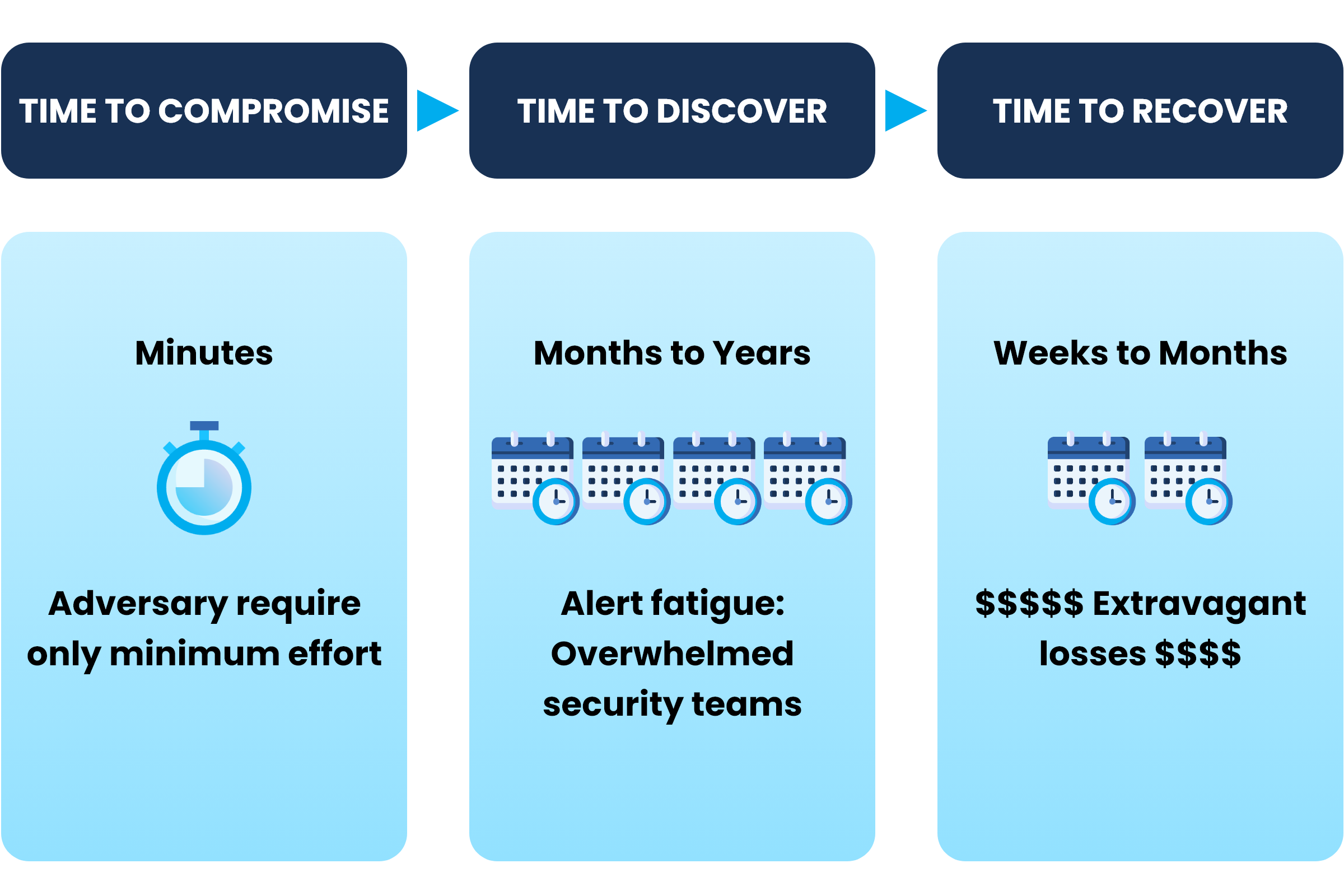
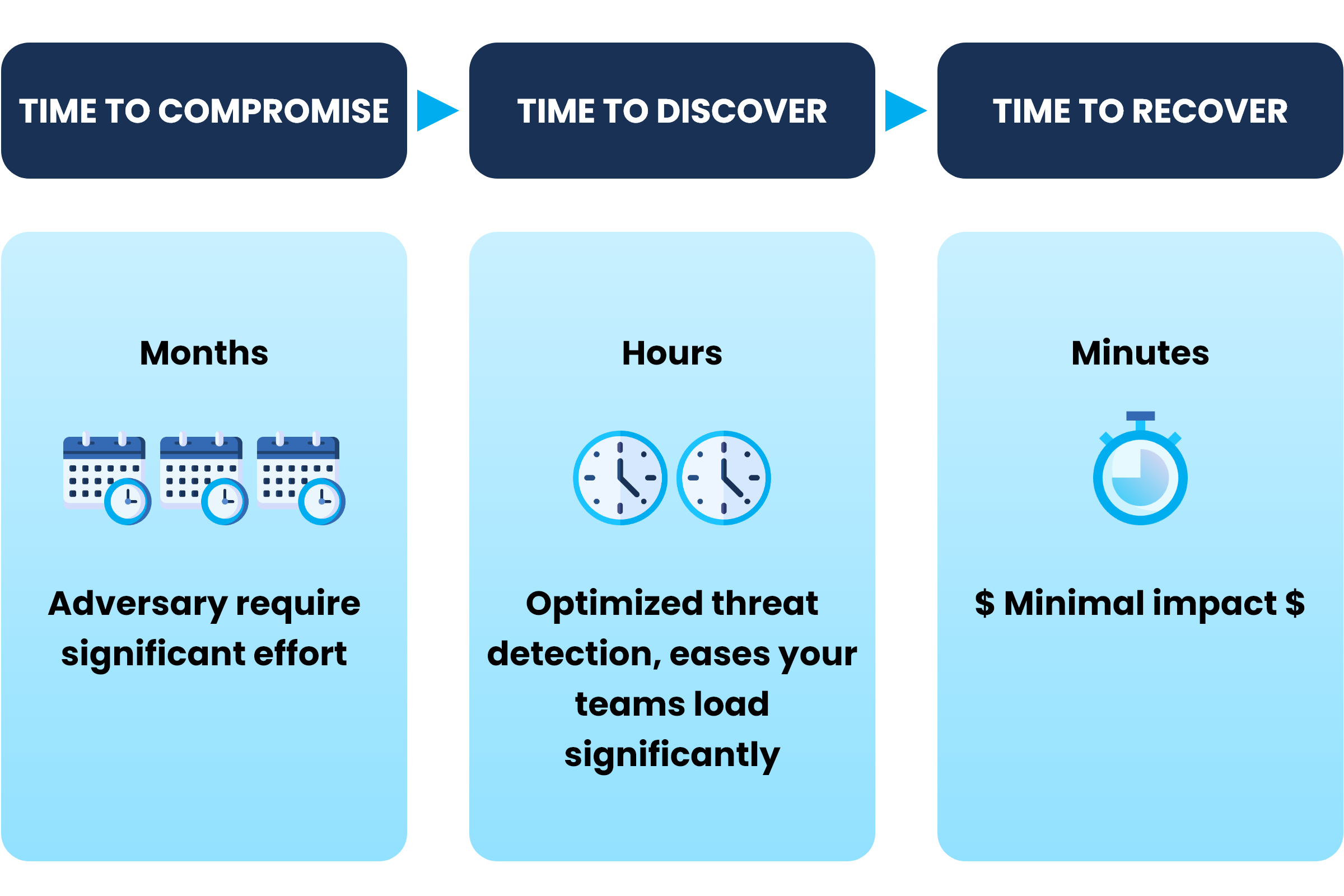
Proactive Threat Prevention: Stop attacks before they cause harm with AI-driven threat detection and automated response capabilities.
Proactive Threat Prevention: Stop attacks before they cause harm with AI-driven threat detection and automated response capabilities.

DefenceScout - Our Platform
Fortify Your Digital Fortress with Our Cutting-Edge Cyber Defense Platform